However, Internet scams do continue to pose a serious security problem, as cybercriminals take every opportunity to obtain financial gain from their victims, exploiting their lack of knowledge and the vulnerabilities of their computers. Cybercriminals take no time off. Cybercrime never rests.
In recent months we have seen here in Spain how cybercrime not only has not ceased but criminals have been constantly stepping up their game to get hold of their juicy illicit profits.
Most commonly, cyber fraudsters send messages, emails etc., posing as specific companies, banks or official bodies in order to gain recipients’ trust and convincing them to share data that will allow the offenders to access the victims’ bank accounts.
One of these latest scams affected the Spanish tax authority during the 2021 income-tax filing season. Posing as tax officers and members of the Ministry of Finance, cybercriminals conducted a large-scale phishing (email) and smishing (SMS messages) attack.
They tried to steal users’ personal data and bank details through messages, mainly alerts; once a user clicked on the link to provide the requested information or to correct the alleged errors, a malicious file was downloaded, which either infected the computer system or blocked it, only to demand money or ransom (ransomware).
These messages featured official logos, the links were styled as if they were authentic, the texts did not contain major spelling mistakes (a usual giveaway in such cases), they used the same email formats as the original ones and very similar domain names.
Here are a few examples of the variety of forms these messages took:

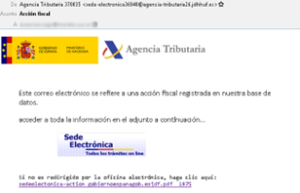
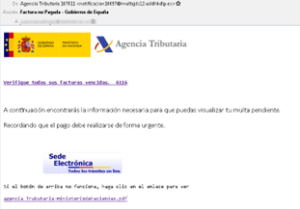
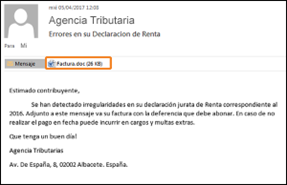


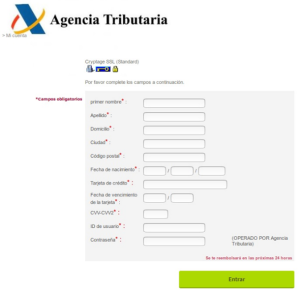
A second case that has sparked alarm is a new Trojan (a type of malware disguised as genuine software that attempts to infect a computer and alter its files and data) that attacked customers of banks such as Banco Santander, CaixaBank and UniCredit.
Similar to other malware, it enters devices via SMS messages in which the cybercriminals pose as the bank in question. Strikingly, the sender of these messages is usually one of the victims of the scam, whose mobile phone has been taken over remotely to access the contacts list and enable the permission for sending messages.
From the moment the user clicks on the link, the virus, connected to a Russian server, may appear in several different forms. This virus is highly capable of stealing credentials and cookies as well as bypassing multi-factor authentication codes, such as Google’s two-step login verification system. Moreover, by obtaining permission from the victim’s own device, this virus has the ability to perform actions without the need for user interaction.
Finally, there has been news about another type of virus that is affecting on a large scale people who are seeking employment. Taking advantage of the situation in Spain, where the number of unemployed is considerable, cybercriminals send out links offering enticing jobs, promising good working and financial conditions. When a job seeker opens the link, the virus is deployed on the device and gains access to the victim’s bank accounts.
Against this backdrop, the most recommendable – and probably only – approach is to be constantly alert, cautious and well informed about current cybersecurity issues. Messages, their senders, subject lines, URLs etc. should always be carefully checked. If in doubt, never open a link but delete it and use the official communication channels to contact the company that supposedly sent the email/SMS, to verify whether the message is authentic or not.
If, however, the infected file has already been downloaded or even executed, the most important steps are to get in touch with a company specialising in cybersecurity, try to disinfect the device or network, search the Internet to see if personal data has leaked and, finally, to take legal action to track down the offender and make the authorities aware of this type of scam so that they can investigate it and alert citizens.